Fighting Fraud with SentiLink's Naftali Harris
PayPal's 4.5m "Illegitimate" Accounts, $320m DeFi Hack, Klarna's Charge Card, More Banks Axe Overdrafts
Hey all, it’s Jason.
I’m finishing up this week’s issue on an *exceptionally* dreary Sunday here in the Netherlands. I guess one upside of the winter weather here in the lowlands is that I’ve managed to focus long enough to read entire books, instead of my typical reading diet that consists mostly of newsletters and tweets.
I recently completed Cashless, by Richard Turrin, which I recommend for anyone interested in China, the origins of super apps, or potential applications of CBDCs. Have a recommendation for what I should read next? Let me know!
Existing subscriber? Please consider supporting this newsletter by upgrading to a paid subscription. New here? Subscribe to get Fintech Business Weekly each Sunday:
PayPal’s 4.5 Million “Illegitimate” Accounts
PayPal reported quarterly earnings last week, and, while the company generally had a strong 2021 and Q4 (though it traded down 23% following the earnings release), one data point stood out: the payment processor noted its miss in net new active (NNA) transacting accounts was driven in part because of some 4.5 million accounts it had determined were “illegitimate.”
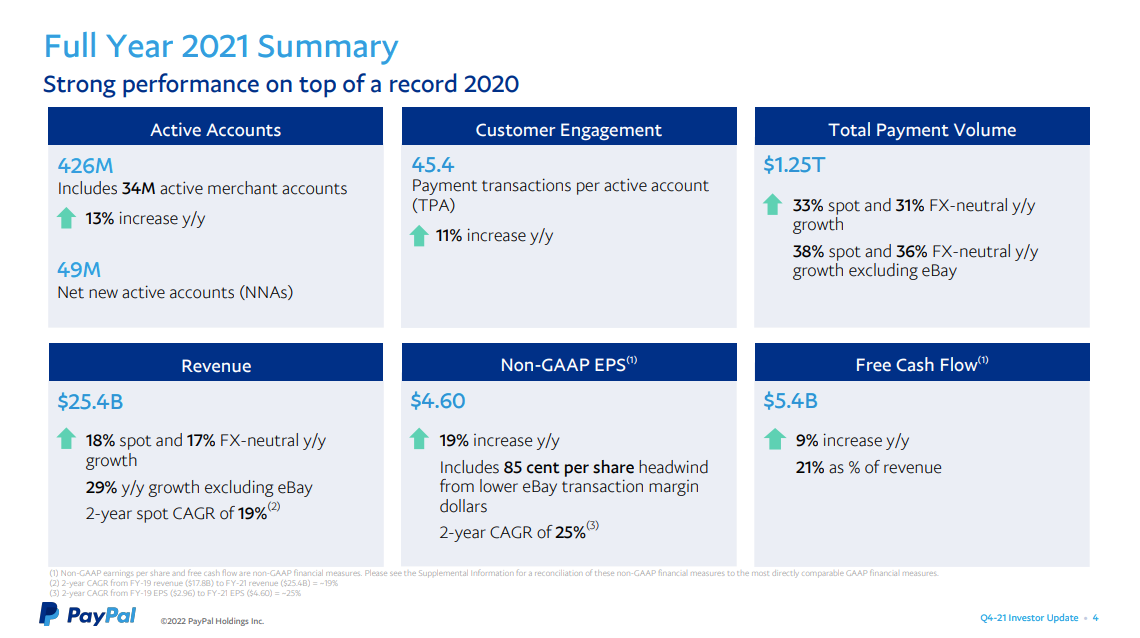
In remarks on the earnings call, PayPal CFO John Rainey further clarified that incentive marketing campaigns offering sign up bonuses drove the spike in “illegitimate accounts” (emphasis added):
“For context, we regularly assess our active account base to ensure the accounts are legitimate. This is particularly important during incentive campaigns that can be targets for bad actors attempting to reap the benefit from these offers without ever having an intent to be a legitimate customer on our platform.
In the fourth quarter, in connection with the increased use of incentive campaigns throughout 2021, we identified 4.5 million accounts that we believe were illegitimately created.”
On its buy side analyst call, Rainey pointed the finger at “bots that are creating multiple accounts” in order to collect sign up bonuses.
Sign up incentives have a long history in consumer financial services. The difference in the digital era, as always, is scale.
PayPal understandably didn’t explain the exact weaknesses that were exploited. But, given the ease of digital account opening and of obtaining stolen identity credentials, conducting this type of fraud in an automated fashion, at large scale, is clearly feasible.
PayPal is far from the only service offering referral or sign up bonuses. Popular neobanks like Chime, Varo, Current, and Revolut have run incentive-based campaigns at various points in time.
In theory, the requirements to qualify for these referral and sign up bonuses — which can reach a total of $200 — are more onerous, including requirements like a minimum of $200 in direct deposits to a newly opened account. The measure is designed to encourage new users to move their payroll direct deposit in order to get the bonus payment.
But, in practice, pretty much any ACH deposit will trigger the bonus — as detailed by numerous websites like this one that explain how to harvest these kinds of bonus offers (emphasis added):
“While the terms do say a direct deposit is required, in practice, an ACH push from almost any external bank account will trigger the direct deposit requirement and get you your bonus.
To do this, you’ll want to go log into your non-Chime bank account, link your Chime account to that bank account, then transfer $200 or more into your Chime account. If the transfer works, then the bonus should post instantly, but at most, within 2 business days.”
Many neobanks, most of which are still private, and thus have few disclosure requirements, often tout their growing user numbers.
But with referral + sign up bonuses that are up to 10x as large as what drove PayPal’s spike in “illegitimate accounts,” one has to wonder if some neobanks’ user numbers aren’t also inflated by bogus accounts.
Fighting Fraud with SentiLink’s Naftali Harris
The COVID-19 pandemic has come with a truly unprecedented increase in fraud taking place online. There are a variety of reasons why, including the rapid upswing in consumers transacting online instead of in person, financial services companies quickly transitioning to work from home, and trillions of dollars of hastily disbursed government aid in the forms of expanded unemployment, stimulus checks, and PPP loans — which made ripe targets for fraudsters.
One company on the front lines of detecting and mitigating various types of fraud risk is SentiLink. I had the opportunity to ask co-founder and CEO Naftali Harris some questions about why fraud has become such a pervasive problem in digital financial services lately. What follows is our written interview.
Jason: You were an early employee at Affirm, where you were involved in building out various risk functions. What were some key learnings from your time at Affirm? How did that experience give rise to SentiLink?
Naftali: I was the first data scientist at Affirm, and Max Levchin (Affirm’s CEO) put me in charge of building out the Risk Decisioning team. It was definitely more responsibility than I deserved at the time but a terrific crash course in risk, fraud, and credit.
One of the key learnings from my experience there was the existence of synthetic fraud, (when fraudsters apply using a fictitious rather than a stolen identity). Prior to seeing this myself, I didn’t even know this was possible. When we discovered this issue, my then-colleague and now co-founder Max Blumenfeld and I realized there were huge, unsolved issues in the risk world and decided to build SentiLink to solve them.
Jason: The term “fraud” encapsulates a variety of risks at different points in a customer journey. Risks include during account opening, account takeover, transactions, returns, disputes, and so on. What aspects of the customer lifecycle is SentiLink focused on?
Naftali: Right now we are focused on the account opening process. We work with over 100 financial institutions ranging from top-ten banks to new startups and process around a million new account applications each day.
Jason: SentiLink is best known for helping firms detect synthetic identity fraud, where a credit bureau profile that isn’t tied to a real person is used to open accounts or apply for loans. For readers who are unfamiliar, can you describe the basics of how this is possible?
Naftali: It’s surprising easy (though don’t go do this at home–it’s a felony):
First, you make up a fake person. Inventing the name and DOB is easy, as is signing up the identity for a phone number and email, but a lot of people imagine that the SSN would be hard to get. Actually, they’re nine-digit numbers and most of the billion possibilities are potentially valid SSN’s, minus certain publicly known exceptions such as SSN’s that begin with the digit 9 (which are ITINs). Until June 2011, the first five digits could tell you the state and year range in which the SSN was issued. This is public information as well and so fraudsters will typically use an SSN that could have been issued in the last 18 years, so that even if it does belong to someone it will be a minor who is not competing with the fraudster for use of the SSN.
Secondly, you start applying for credit with the synthetic identity, even if you get rejected. Most people don’t know this but actually the act of applying for credit will create provisional credit reports at the bureaus. Eventually the fraudsters are able to get their identities added to the bureaus.
Thirdly, you boost the synthetic identity’s credit. It’s possible to do this very quickly, for example, by purchasing authorized user tradelines for the synthetic identity.
Finally, you use that synthetic identity–which now has good credit–to apply for loans and not repay.
Doing this has become so commonplace that you can now even find tutorials for how to do this online.
Jason: But SentiLink’s offerings go beyond this – what other capabilities does SentiLink provide?
Naftali: We also help to detect ID theft, help satisfy obligations from the various KYC/CIP regulations, were the first company to go live with eCBSV, and have some products we’re developing around first party fraud.
Jason: What is different about detecting a stolen identity vs. synthetic?
Naftali: They’re two fundamentally different problems–for synthetic fraud, you’re checking whether the identity that is being used to apply is cohesive (i.e. all belongs to the same, real person). But with ID theft you’re checking whether the identity that is applying actually belongs to the person who is applying.
As a result, lots of the things you do to prevent ID theft (such as checking if there is a phone number that ties to the identity that the applicant can prove they control) don’t work for preventing synthetic fraud. Conversely, most things that prevent synthetic fraud don’t work for ID theft, given that fraudsters steal the identities of real people.
One other particular challenge with synthetic fraud compared to ID theft though is that ID theft has a direct consumer victim, who often eventually finds out that their identity has been misused and alerts the relevant financial institutions. Synthetic fraud doesn’t have that same direct consumer victim, and so losses associated with synthetic fraud can often go undetected and mistaken for credit losses.
Jason: What is the relationship between “fraud” and other fin-crime risks, like money laundering?
Naftali: They’re all related, given that oftentimes the same fraudsters are committing them. In particular though, account opening fraud at institutions that allow money transfers (including checking and savings products, money transfer products, crypto exchanges or wallets, and even brokerage or other investment products) facilitates money laundering.
Jason: Why aren’t KYC/AML checks sufficient to stop fraud?
Naftali: They actually are sufficient, just not in the way that some in our industry are interpreting them. If you read the CIP rules (https://www.law.cornell.edu/cfr/text/31/1020.220), they say quite simply that you must establish procedures that enable you “to form a reasonable belief that [you] know the true identity of each customer.” Obviously, if an organization is letting through a lot of identity fraud, (either ID theft or synthetic fraud), then those procedures clearly did not allow them to form that reasonable belief and arguably that organization is not in compliance. It’s a bit of a tautology, but the CIP rules actually do require you to have procedures that are reasonably good at stopping fraud!
Unfortunately, some in the industry interpret the CIP rules as requiring you to check for a “match” of the four CIP elements (name, DOB, SSN or other identifier, and address). In addition to complying with neither the letter nor the spirit of the CIP rules, as typically implemented these “match-based” checks are also nearly useless at stopping fraud.
For synthetic fraud, the reason they are so ineffective is that a “match” is typically defined as the identity having some prior financial records, which under the hood usually means they have a credit report. Because the fraudsters are easily able to create these records for synthetic identities, these “KYC checks” will always return matches on all four data elements.
For ID theft, the reason these match level checks are so ineffective is that the fraudsters steal identities of real people, whose name, DOB, SSN, and usually address will match their preexisting financial record. Of course, the fraudster is the one submitting the application but there’s no way to tell with these data elements.
SentiLink’s KYC Insights product takes a first principles approach to KYC compliance–starting with literally reading the regulations–to help financial institutions fight fraud and comply with the CIP and red flags rules.
Jason: Fraud is a pervasive problem in the US banking and fintech ecosystem – something that was turbocharged during COVD-19. What events/trends of the pandemic gave rise to this massive spike in fraud? Who’s responsible? What can be done to better mitigate it?
Naftali: There were really two issues that caused this.
Firstly, the PPP program was designed to move as much money to deserving businesses as fast as possible, prioritizing speed and availability over risk controls. The government guarantee of these funds to participating lenders in particular removed nearly all of the financial risk to the lenders, who were encouraged by policymakers to push money out the door as quickly as possible. Given the strong public interest in helping struggling businesses, on the whole this was not necessarily bad policy from Congress, but the speed and urgency did lead to a downside of increased fraud levels.
Secondly, many of the unemployment insurance programs offered by the states turned out to be very poorly designed from a risk perspective when stress tested. In some of the cases, the states were not doing very basic checks, and their UI risk programs would shock anybody with even a passing interest in fraud and identity. Not only did a lot of them let through an enormous amount of fraud, but there were also numerous reports of citizens who had a hard time acquiring the benefits to which they were entitled. Better controls here (both from a loss mitigation perspective as well as a customer experience perspective) would help.
Jason: There’s a perception that “fintechs,” especially neobanks and wallets, are more susceptible to fraud than “incumbents” (banks). In your experience, is that perception accurate? Why would this be the case?
Naftali: No. I’ve seen traditional financial institutions with very high and very low fraud rates, as well as fintechs with very high and very low fraud rates. In general, traditional financial institutions often benefit from institutional experience–their people and their systems are inoculated against fraud attempts they’ve seen even 10+ years prior. But fintechs often are faster moving and have more creative controls.
Jason: How does fraud risk vary by product type? Eg, bank account vs. installment loan vs. pay-in-4 BNPL?
Naftali: This varies over time based on what the fraudsters choose to target. For example, at the height of the pandemic we saw a huge influx of fraud in checking and savings accounts, related to fraudsters stealing identities and opening DDAs in order to launder UI funds they’d stolen.
Jason: Who is bearing the cost of fraud? How is this liability determined?
Naftali: For most of the account opening fraud that we tackle, losses are borne by the financial institution where the fraudster opened the account. For example, when a fraudster steals an identity and uses it to open a credit card, the credit card issuer will be liable for any balances that the fraudster runs up and doesn’t pay.
Jason: What role do (should? can?) regulators play in addressing fraud?
Naftali: The most important role regulators should play in addressing fraud is being clear about the regulatory obligations financial institutions have in stopping fraud, and offering more clear guidance about these rules. Ultimately, financial institutions are the ones who operate and control their fraud programs, and so most of the work that needs to happen has to happen at the financial institution.
Jason: Given the sheer scale of transactions, an automated approach (eg models, AI, etc.) is required. But, models inevitably will have false positives (transactions flagged that are legitimate) and false negatives (fraudulent transactions that slip through). How does SentiLink (or, in practice, SentiLink’s customers) think about balancing these, when tuning these models?
Naftali: How organizations think about balancing false positives and false negatives depends on their business and risk philosophy. For example, some customer-centric companies we work with are very sensitive to false positives on returning users, and so will do more up-front verification work and suffer higher false positives for new users, in exchange for tuning models down to be more lenient on returning users. Some companies we work with are very sensitive to only having high quality loans, and so will tune the models to have fewer false negatives and more false positives.
In order to help our partners make the right decisions for them, at SentiLink we actually provide precision, recall, false positive and false negative tables to our partners based on manual reviews that our Risk Operations team conducts. Given that the performance of our scores varies partner by partner, these analyses are actually specific to each partner.
Jason: What is the craziest case of fraud you’ve ever seen? How have you seen fraud vectors evolve since you first began working in the space?
Naftali: Well I’ve seen a whole lot of crazy stuff, but the most recent memorable one was an application for Elvis that we came across a few weeks ago. Whoever was submitting the application even found Elvis’s real SSN and used that as well. It wasn’t a particularly hard case but it was certainly a lot of fun to review!
That particular case aside, the fraudsters have gotten smarter over time and a lot of the fraud that we come across now is more sophisticated compared to a few years ago. Fraudsters are some of the most creative people out there, and at SentiLink we frequently joke that if they decided to employ their talents to better society rather than steal from it then in a few years we’d all be enjoying our flying cars.
Jason: How do you think identity verification will evolve? Defi? Digital driver’s licenses? What opportunities and risks do new technologies like these pose in the effort to mitigate fraud?
Naftali: I think there will be increased centralization of identity over time. Right now identity is so fragmented, with each part of someone’s identity stored in a different place. Being able to connect those fragmented parts of someone’s identity can have a huge impact and enable us all to prove who we are more seamlessly. I believe that over the long run as society gets better at identity verification, authentication will even come to many (non-financial) contexts where there previously wasn’t any identity verification simply because of difficulty and expense.
Jason: Anything I haven’t asked about SentiLink that I should have?
Naftali: You didn’t ask how we name our conference rooms! They’re named after chess grandmasters, including Kasparov, Polgar, Tal, and Carlsen.
FT Partners Super App Deep Dive
Frequent readers of this newsletter will know I’m a bit bearish on the idea of a so-called “super app” emerging in the US, for reasons I explored previously here.
Still, FT Partner’s dropped a 131 slide deck last week exploring “The Race to the Super App,” and even if I disagree with some of the arguments, it is well worth a read to understand how many in the fintech space are thinking about the “super app” opportunity.

DeFi’s $320 Million Hack
Another week, another multi-million dollar crypto hack.
In just the past few months, we’ve seen Crypto.com lose $34 million of customer funds due to a bug in how it implemented two-factor authentication, BitMart lose $196 million due to a security breach, and users of NFT platform OpenSea lose millions due to product and design flaws in how NFT listings are handled.
In each of these cases, users were reimbursed from the companies’ own funds (or are supposed to be reimbursed, anyway.)
The latest crypto catastrophe? Wormhole, a “blockchain bridge,” had $320 million worth of ether stolen in a hack.
Wormhole is a cross-chain bridge that enables users to trade assets from the Solana blockchain directly into other cryptoassets via ethereum. Ethereum creator Vitalik Buterin has expressed skepticism about such cross-chain bridges, citing “fundamental security limits of bridges.”
In this incident, attackers were able to mint (create) 120,000 wrapped ETH (wETH) “out of thin air” on the Solana blockchain, of which they were able to move 93,750 to the ethereum blockchain.

The pilfered funds were quickly replaced by Wormhole parent company, high-frequency trading shop Jump Trading.
Still, this adds to the now more than $2 billion lost in DeFi hacks and exploits. While, in this case, users were made whole as the company footed the bill for the stolen crypto, users are reliant on the ability of impacted companies to bear the losses when funds are stolen.
It isn’t hard to imagine a hack large enough that a company won’t — or can’t — reimburse users’ losses.
Other Good Reads
Digital Land Grab: Metaverse Real Estate Pries Rose 700% in 2021 (Ron Shevlin/Forbes)
Fireblocks $8B valuation on $45B AUC; Wealthfront is UBS' third roboadvisor (The Fintech Blueprint)
Fintech Fire Alarms: January (Fintech Takes)
Contact Fintech Business Weekly
Looking to work with me in any of the following areas?
New: Product strategy or go-to-market consulting
Sponsoring this newsletter
Content collaboration or guest posting
News tip or story suggestion
Early stage startup looking to raise equity or debt capital
Feel free to reach out to me: jason@fintechbusinessweekly.com
Looking for Klarna’s Charge Card and More Banks Axe Overdrafts?
There’s more Fintech Business Weekly below for paying subscribers👇 — if you already subscribe, thank you for helping make this newsletter possible




